Be it user data or an organization’s data, it is the first priority of an organization to take preventive measures to secure it from cyber crimes nowadays. The reason for this consideration is that technological advancements have also led to high-scale cyber crimes. In this regard, user authentication is one of the finest methods that has helped businesses and firms secure data in an effective manner. In this article, you will find many topics revolving around the topic of user authentication.
What is User Authentication?
By definition, user authentication is known as the process that helps protect a user’s data from scammers or hackers. This is mostly achieved by implementing types of authentication methods that require a user to submit some kind of information that works as evidence of their identity and grants them access to the system.
Example
A common example of user authentication practices is the requirement of credentials like email addresses or passwords once a user tries to get access to their social networking accounts like Instagram, Facebook, LinkedIn, and many others. Not only social media accounts, but all sorts of mobile applications or digital mediums ask for a piece of evidence to ensure or verify the presence of the actual account holder and not someone who is acting to own the account.
How Does User Authentication Work?

No matter what kind of user authentication method an agency opts for, the basic working mechanism of these systems is quite similar and is divided into four steps.
-
First Step: Requirement Of Credentials
The first step requires the user to enter their login credentials, for instance, username, password, email address, etc., for the purpose of identity verification.
-
Second Step: System Verification
The second step involves the system decrypting the information the user has provided. In simple words, the system compares the information with the stored credentials to verify the user’s identity.
-
Third Step: Granting Access To The System
Once the information matches the stored credentials of a user, they are granted access to log into their account. Otherwise, the user is alarmed about submitting incorrect information.
-
Fourth Step: Preventive Measure
The fourth step is not required to be followed if a user is granted access to their account in the third stage. However, in a contradictory situation, the user might be granted another option to type in their credentials or might be blocked out of the system, depending on the number of trials as well as the security policy.
Check Out These:
- Why is Fansly Better Than OnlyFans?
- Choosing Cross-Platform Development: An Overview
- Software Development Team
What Are The Steps That Help In Setting Up A User Authentication System?
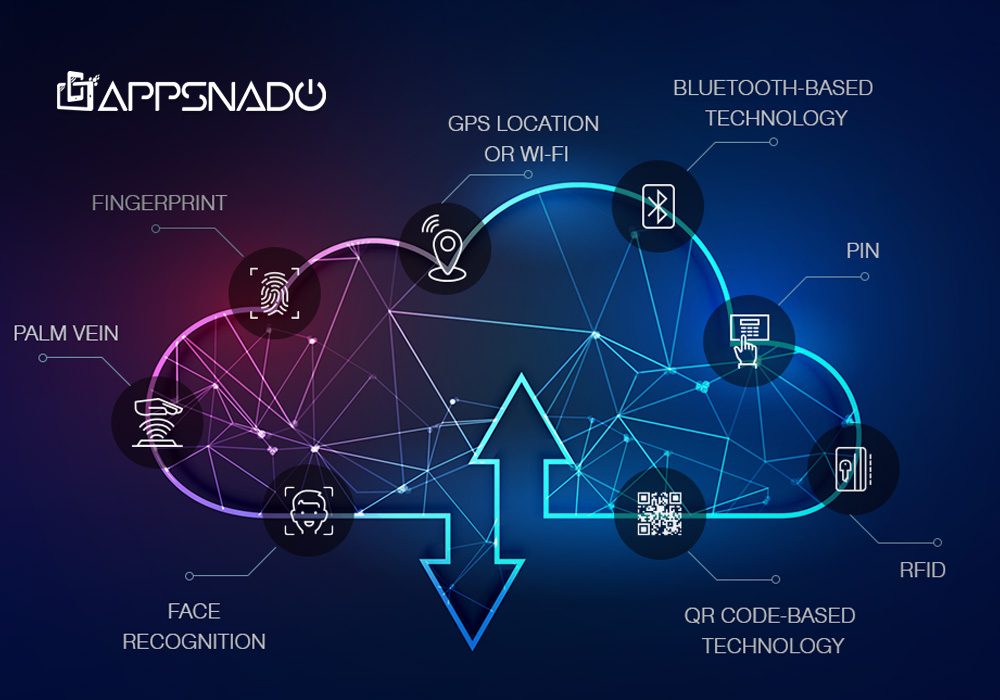
Moving forward in the article, we will now explore the process that is followed to set up the user authentication system easily.
- First Step: Selection of Authentication Method
- Second Step: Installation of the System
- Third Step: Navigate the System
- Fourth Step: Testing
-
First Step: Selection Of Authentication Method

The first step to setting up a user authentication system requires the development team to explore the authentication methods and select the type that is perfect for the cause.
-
Second Step: Installation Of System

After selecting the user authentication method, the team of software engineers will move further with the process by installing the software system and setting up user accounts.
-
Third Step: Navigate The System

Once the system is installed, the developmental team of professional software engineers and others shall navigate the system properly to set security parameters such as the minimum password complexity, session timeouts, and lockout rules.
-
Fourth Step: Testing

After setting up the entire system according to the organization’s needs and requirements, the user authentication system shall undergo a testing phase in order to ensure smooth functionality without any bugs or errors occurring before it is launched into the system.
Check Out These:
- Guide To How Much Is A VR Headset For Xbox One
- Mastering Angular SEO
- Quality Control Vs Quality Assurance
What Are The Types of User Authentication?
After discussing what is user authentication, how it works, and the procedure to set up an authentication system, we will move on to the next topic, which is the types of user authentication methods.
- Type No. 1: Password-Based Authentication Method
- Type No. 2: Multi-Factor Authentication Method
- Type No. 3: Certificate-Based Authentication Method
- Type No. 4: Biometric Authentication Method
- Type No. 5: Token-Based Authentication Method
-
Password-Based Authentication Method
The first category of user authentication methods is known as password-based authentication. In this process, a user is required to set a password that includes letters, numbers, or special characters. With the help of the password, a user will be able to have access to the system.
The shortcomings of the password-based authentication method include:
- Users set common or simple passwords that are easier to remember.
- Users set a single password for multiple platforms.
- Scammers and hackers easily figure out a simple password after a few tries, which leads to cybercrimes like phishing attacks, identity theft, data theft, etc.
-
Multi-Factor Authentication Method
By its name, it is easier to understand that this type of identity verification includes more than one authentication method for users to get access to their accounts.
With the help of the multi-factor authentication method, companies and businesses get the following benefits:
- Organizations get the chance to add layers of protection to secure data and save it from different kinds of cyber crimes.
- Multi-factor authentication can include methods like codes generated from a user’s smartphone, captcha tests, patterns, passwords, biometrics, facial or voice recognition, and fingerprints.
- This method is known for its benefit of increasing user trust as well as high-quality security measures.
-
Certificate-Based Authentication Method
Next in line, we have a certificate-based authentication method that might not be applicable to most of the social networking platforms we use commonly in our day-to-day lives. However, this authentication method is still considered to be an effective way of verifying identity.
A certificate-based authentication system will require the user to submit a digital certificate while trying to get access to their account. These e-certificates are similar to a driver’s license or a passport. Electronic certificates include elements like a user’s digital identity, a digital signature from the certifying authority, or a public key.
A factor that makes this user authentication method reliable is that digital certificates are only granted by certified authorities, which means not everyone can give out these documents easily or have access to them. Once the e-certificate is submitted, the server confirms the validity of the certificate authority and the digital signature to give access to the account.
-
Biometric Authentication Method
Biometric authentication is becoming more popular day by day. Many companies and businesses are now considering utilizing this authentication method as it ensures a peak level of data security and safety.
The working mechanism that the biometric authentication method utilizes includes the individual features of a user to verify their identity and grant access. The reason why it is preferred by organizations is that you can add this method to multi-factor authentication, compare the information with already stored database information, and use it digitally as well as on-site.
In this regard, an organization can opt for different types of biometric authentication methods, including face recognition, voice recognition, fingerprint scanners, or eye scanners. All of these categories identify the various features of an individual and compare them to the stored data to grant access without any hassle.
-
Token-Based Authentication Method
Last but not least, we have token-based authentication in the list of types of user authentication methods.
This system requires users to enter their credentials once and get access to a special encrypted string of random characters known as a token. The token allows users to get access to their accounts as many times as they want, rather than repeatedly inputting their credentials. In other words, a token works as proof that you have already been granted access.
Check Out These:
What Are The Benefits of User Authentication Methods?
In the last section of the article, we will review some of the exceptional benefits of user authentication methods.
- Improvement Of Security Measures
- Increased Trust Of Users.
- Protection Against Various Cyber Crimes
- Helps In Following Laws Correctly.
- Track Of User Behavior.
-
Improvement Of Security Measures
The first benefit of a user authentication system is that it protects the entire security system of an organization. With the help of these methods, companies and businesses can now make sure that only authentic, verified users can log into their systems, networks, and applications.
-
Increased Trust of Users
The second benefit that different types of authentication methods provide is increasing the trust of users in an organization. Once a user witnesses how seriously a company or business takes its data security, there is a high chance that they will always opt for your services rather than others.
-
Protection Against Various Cyber Crimes
With the advancement of technology, cybercriminals have also developed new ways of committing crimes. However, with the help of user authentication, organizations can now combat this issue and protect their systems from different crimes like identity theft, phishing attacks, data breaches, etc.
-
Helps In Following Laws Correctly
The fourth benefit of user authentication methods is that they help in following legal data protection rules and regulations that demand reliable user authentication procedures to protect sensitive data. These laws and regulations are a must to be followed by various industrial sectors; hence, implementing authentication methods is necessary for all industries.
-
Track Of User Behavior
Last but not least, types of authentication systems also allow companies and businesses to trace the behavior of users who are accessing the accounts. This information helps in noticing any suspicious activity within the system and taking immediate action against it.
Check out this: Unreal Engine 4 vs 5
Can A Mobile App Development Company Help You Set Up User Authentication Methods In Your App?

Since user authentication has become so crucial for the security and safety of user data, mobile app owners belonging to different industrial sectors are concerned about adding these practices to their applications to gain the trust of users as well as save themselves from major losses.
In this regard, a company or business can easily take help from a mobile app developer or a team of developers that can help them decide which type of user authentication method will suit them the best. Not only that, these skilled professionals will also make sure to follow the right process to install the software and test the functionality of the authentication method once the app is developed.
To Wrap Up: Why Is It Important To Implement User Authentication Methods?
User authentication is important and necessary for both securing user data and identity verification. In the past, we have seen many well-known companies suffer from different kinds of cybercrimes that resulted in massive losses, and it took more than ever to recover from that loss. However, the times have changed, and with that, the preventive measures to secure data have also advanced greatly. In such times, it is essential for companies and businesses to implement the latest means of user authentication for their safeguard as well as progress in the market.
Check Out These:







